The ARCON | Privileged Access Management (PAM) solution provides over every aspect of your IT infrastructure, so that you can build contextual security around your most important asset: data. Its granular access control allows you to structure your security infrastructure the way you want, giving and revoking access for whomever you wish, whenever you wish, all on your own terms.
Control Access to your Data
Secure your Data from
Anywhere
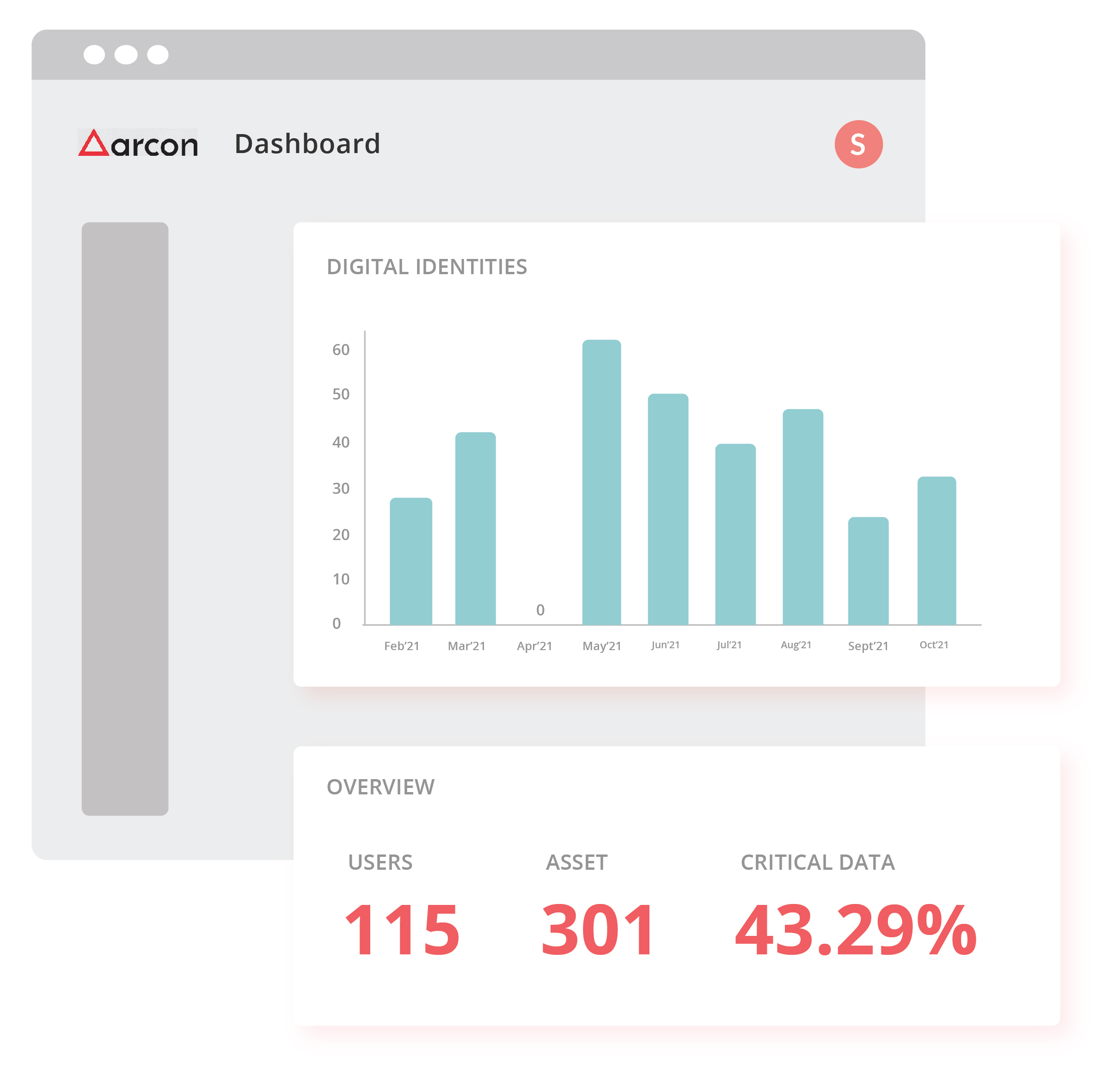
Learn Where your Important Data is
Key features of ARCON | PAM

Single Sign On:
Helps connect to a different category of systems and devices without entering login credentials

Password Vault
Offers a highly secure password vault that generates strong and dynamic passwords and rotates them automatically.
Ephemeral Access:
Automatically generates rule and role based temporary access rights with an Amazon Web Services (AWS) Console or Command Line Interface (CLI) component.

Virtual Grouping:
Provides a dynamic group setting with virtual grouping where you can create functional groups of various systems

Session Monitoring
Provides basic audit and monitoring of all privileged activities through a single command center in real-time.

Security Compliance Management
The ARCON | SCM solution creates and enforces a comprehensive IT risk management framework – a unified engine of all IT risk management controls required to be implemented at different layers for effective risk mitigation. The solution ensures the creation of a robust security posture and ensures compliance. Leave IT Risk Assessment to the Bots Critical technology platforms require continuous risk assessment. This can be achieved through the power of AI – governing, assessing, and optimizing the organization’s Information Risk Management

Endpoint Privilege Management
The ARCON | Endpoint Privilege Management solution (EPM) grants endpoint privileges ‘just-in-time’ or ‘on-demand’ and monitors all end users for you. The tool detects insider threats, compromised identities, and other malicious attempts to breach endpoints. It has a powerful User Behaviour Analytics component that takes note of the normal conduct of end users and identifies atypical behaviour profiles and other entities in the network. Prevent Data Leaks
Get Instant Access to News & Updates!
About ARCON
Solutions
By Industries
By Compliance
By Industries
By Compliance
Resources
Keep in Touch
ARCON is a globally recognized Identity-As-A-Service provider with a wealth of experience in risk management and continuous risk assessment tools. Our award-winning solutions portfolio includes our Privileged Access Management (PAM) solution along with Identity and Access Management (IAM), Endpoint Privilege Management (EPM), and Cloud Governance (CIEM), among others. Our world-class training, deployment, and support help organizations optimize their experience with our solutions right from the procurement stage and configure our solutions to match all challenges to support growth and scalability.
Request A Demo
Feel free to drop us an email, and we will do our best to get back to you within 24 hours.



