When one of the world’s biggest internet companies reported a series of hacks that compromised confidentiality of hundreds of millions of users, it gave a sober warning to cyber community: organizations irrespective of their sizes are extremely vulnerable to cyber incidents.
The cyber incident that involved hacking of about 3 billion accounts was a warning bell. The lesson learnt from that incident was that it is not only critical to have essential wherewithal to deter attacks but organizations should also properly comprehend and timely investigate incidents.
However, organizations, in spite of spending abundant resources on information technology are failing to prevent attacks on one of the most valued resources—information assets.
Indeed, from a global audit company to credit card score reporting organization—all have fallen prey to cyber-attacks.
These incidents, often perpetrated by sophisticated organized hackers, occur repeatedly because organizations behave reactively to decrease the damage done and not controlling it in the first place.
Very often, we hear organizations claiming to have in place robust information systems, yet all these incidents occur because of weak network and data security in addition to organizations’ apathy towards security.
There is a saying: “Put the money where the mouth is”. Organizations need to apply that rule on themselves.
It is imperative for this reason that organizations of all shapes and sizes have an unambiguous policies and practices around data security. In the digital commerce age, highly advanced IT infrastructure will yield productivity gains; however, process improvements will get offset by weak internal security controls.
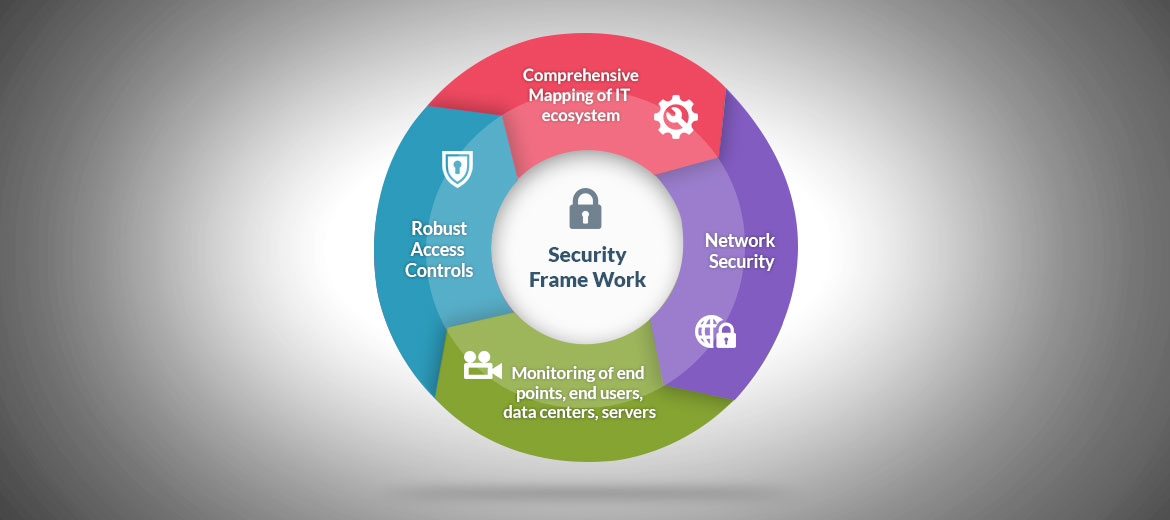
For this very reason, organizations need to relook at their security framework. Stopping advanced attacks is not possible; however, preventing such attacks by having a proactive approach towards systems security is in our hands. This does not mean having a robust security around the periphery to keep network security intact by monitoring malicious traffic.
Equally important is to have a comprehensive mapping of the IT ecosystem. Organizations will need to make sure all endpoints, end-users, data centers and servers are also monitored and defended whilst access control policies are well-defined.
Our suggestion is to apply the “Back to Basics” formula wherein organizations amend security framework by moving back to where it started; that is, safeguarding configurations and identities through applying the “need to know” and “need to do” principles. It is the time to revisit and strengthen access controls.
ARCON is a leading enterprise risk control solutions provider, specializing in risk-predictive technologies. ARCON | User Behaviour Analytics enables to monitor end-user activities in real time. ARCON | Privileged Access Management reinforces access control and mitigates data breach threats. ARCON | Secure Compliance Management is a vulnerability assessment tool.