Zero Trust Architecture: Why is it Unshakable?
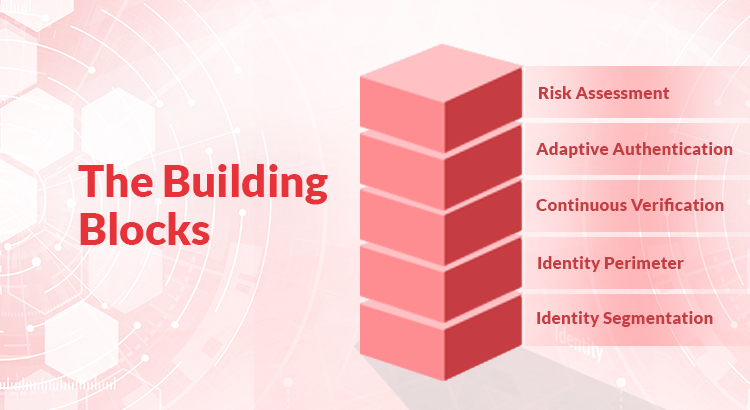
An Overview New technologies and IT infrastructure modernization have extended the boundaries of identity. And these ever-expanding IT boundaries pose a mighty challenge for information security heads. The challenge is not simply to maintain strict identity controls. The bigger challenge is that these ‘trusted identities’ are dispersed in decentralized IT environments. There is a growing […]
