An Overview
New technologies and IT infrastructure modernization have extended the boundaries of identity. And these ever-expanding IT boundaries pose a mighty challenge for information security heads. The challenge is not simply to maintain strict identity controls. The bigger challenge is that these ‘trusted identities’ are dispersed in decentralized IT environments.
There is a growing hodgepodge of applications, systems, APIs, and data that is scattered across IT networks in distributed data centres and multi-cloud environments. This hodgepodge of sensitive information is at constant risk from unauthorized access from vast user population- employees, third parties, and customers.
A single unauthorized access to any of these IT resources from any access point made from any “trusted identity” is enough to shake the foundation of enterprise IT infrastructure.
Against this backdrop, the Zero Trust model, also dubbed the “Zero Trust Approach” (ZTA), is assuming a lot of importance in the overall cybersecurity framework. When implemented properly; the Zero Trust Approach (ZTA) can help build an unshakable IT infrastructure.
Why is the “Zero Trust Approach (ZTA) so crucial in today’s enterprise IT context?
Once an organization opts for any new technology, the employees are the ones who drive the day-to-day tasks on disparate applications and systems. IT operations and administration staff define role-based attributes and create identities for end users.
At this point, the organization does not have any choice but to “trust” the end users who can manage the new systems. Having said that, the question here is how to assess or understand the “trustworthiness” of the end user. An end user can be a compromised insider, or an unscrupulous third party.
That’s why IT security practitioners show their immense concern over who should be trusted and who should not be. Further, in a heterogeneous IT environment, it is never easy for IT administrators to ensure trustworthiness while hundreds of users regularly access multiple systems and applications for different purposes at different points of time.
Organizations always want to ensure that each end user access is genuine and authentic. However, does every access is verified before allowing access? If not, then the risk is huge. Hence, we can say that “risk” is directly associated with “trust”.
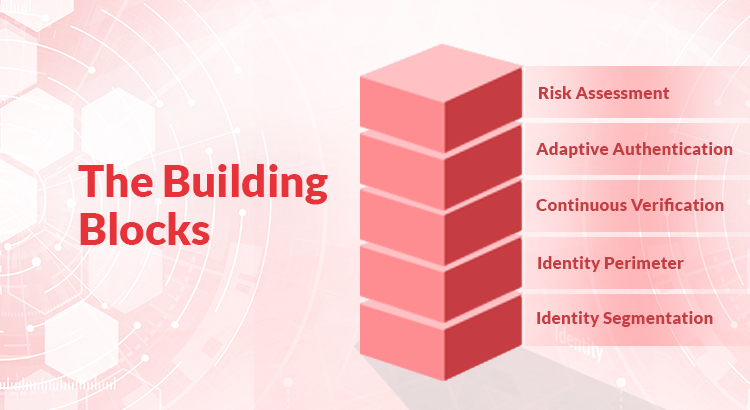
The Zero Trust Approach is based on the principle of “Deny Access” unless the trust is verified at every step. The Zero Trust journey requires careful planning and implementation. Essentially there are five building blocks to construct a Zero Trust architecture. Each building block helps to mitigate the risk of unauthorized access stemming from heterogeneous and distributed IT environments.
How ARCON helps build the Zero Trust Architecture?
At ARCON, our focus has always been on building Access Management solutions that complement the Zero Trust Approach (ZTA). These solutions are built on the credo – “we trust you, but we will continuously assess the trust”.
The table below suggests how ARCON IAM stack constructs the Zero Trust architecture. The table below also shows how the risk vector expands in the absence of Zero Trust Approach.
| WITHOUT Zero Trust | WITH Zero Trust with ARCON |
| Without Zero Trust architecture, organizations remain deprived of micro-segmentation of the large number of identities in the enterprise network. As a result, there are no proper mechanisms to keep track of registered users and there is a risk of iteration of identities (over privileges) across the Line of Businesses (LOBs) and IT functions. | With Zero Trust architecture, organizations can build a robust micro-segmentation of identities that minimizes access control vulnerabilities. With micro-segmentation, organizations can:Ensure rule and role-based access to systems by segmenting users based on LOBs and IT functions Automate the segregation of identities based through virtual grouping toolFurther, ARCON’s Zero Trust architected solutions use network overlays, network encryption, software-defined perimeter, and host-based agents to achieve network segmentation and micro-segmentation of identities |
| The absence of Zero Trust architecture means there are no micro-perimeters of identities where each end-user is bound by the limitations of access. As a result, there are higher chances of losing track of who is accessing what and for what purpose. It invites insider attacks. | With Zero Trust architecture, organizations can build micro-perimeters through policy enforcement and defining entitlements of every identity in order to limit end-user access. ARCON offers:The deepest granular level of control over the identities; helps organizations to ensure every access to the critical system and application is regulated by internal policies Also, ARCON offers a Just-In-Time Privilege approach that removes the risks from the “Always-on” privilege practice and makes sure that there are no standing privileges in the enterprise network.This way, the Least Privilege principle is followed, and there are micro-perimeters around the identities to build the foundation of the Zero-Trust framework. |
| Without Zero Trust, continuous verification of the “trust” of the identities is not possible. The amount of risk surmounts if the verification of identities remains a one-time procedure. There must be a continuous verification of the identities to stop any chances of anomalies. | With Zero Trust, continuous verification of trust is ensured. ARCON helps:The IT administrators review the service access granted to the users regularly to perform various tasks. In case of anomalies, the admins can modify the details of the user access and terminate the session immediately. This way, a holistic user governance framework is built and maintained across the network. |
| No Zero Trust means no Adaptive Authentication. That means, there are no chances for the IT security teams to detect the geographic location and IP address of the end-user device. Hence, any anomalous activity around the user remains undetected and the risk multiplies. | With Zero Trust, organizations can have Adaptive Authentication that helps to assess and re-assess the trust (or authenticity) of the end-users at multiple levels to ensure that the right person is allowed access to the right system for the right purpose at the right time. ARCON offers:An adaptive authentication mechanism that detects and identifies the geographic location and the IP address of the end-user device is considered a criterion to establish the “trust” of the user. |
| Without Zero Trust, organizations miss out on continuous risk assessment of identities in the IT infrastructure. As a result, the organizations remain unaware of any untoward cyber incident. | With Zero Trust, organizations can ensure continuous risk assessment of identities. It eliminates the risk of anomalous activities between random verifications. ARCON offersMachine-Learning-based technology Knight Analytics that detects and displays anomalies in the logged data continuously and generates risk scores based on their behaviour and displays the percentage of risk to the administrator.Spection is another dynamic reporting tool that mitigates security risks that come from longer timelines, and complex workflow matrix in the identity access management space. |
Conclusion
The user access control framework in an enterprise network is always vulnerable due to “assumed trust.” With Zero Trust architecture, organizations can ensure “verified trust” in every layer of the access management space.