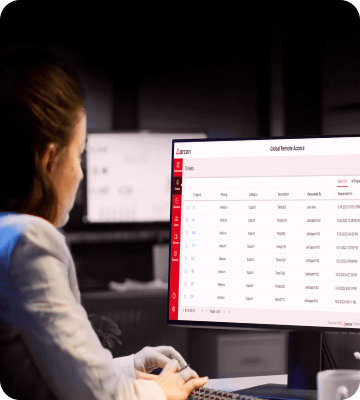
ARCON Global Remote Access (GRA)
Digital nomad, geek, or remote corporate user… whoever be the end user, ARCON | GRA ensures seamless remote access to systems, securely

Baky
A super mom loves to find a balance between Daycaring her two small children and work. She works remotely

A super mom loves to find a balance between Daycaring her two small children and work. She works remotely
Baky
Sreenivas
An admin who yearns for an intuitive dashboard and workflow management to manage remote users

An admin who yearns for an intuitive dashboard and workflow management to manage remote users
Sreenivas

Kenneth
A project manager who frequently requires privileged access to target systems. Currently cannot be on-premises due to personal reasons

A project manager who frequently requires privileged access to target systems. Currently cannot be on-premises due to personal reasons
Kenneth

Nazeer
A security pro he is all for work from anywhere but not at the cost of security. He wants detailed logs and reports for every remote access

![]() A security pro he is all for work from anywhere but not at the cost of security. He wants detailed logs and reports for every remote access
A security pro he is all for work from anywhere but not at the cost of security. He wants detailed logs and reports for every remote access
Nazeer

Antonio
A digital nomad who loves beaches and is a brilliant developer

A digital nomad who loves beaches and is a brilliant developer
Antonio
“As of late 2022, 66% of enterprise leaders have adopted anywhere or hybrid work. This trend will continue as leaders and employees see the benefits of flexible work models.”
– The Forrester Tech Tide™: End-User Computing, Q1 2023
ARCON | Global Remote Access: Provide the ‘outside world’ with access to ‘inside’ IT infrastructure for administrative tasks, maintenance, and support in the most secure way.
ARCON GRA removes the hassles of implementing Virtual Private Networks or any additional installations and
provides robust features to securely as well as efficiently navigate through remote access use cases.
provides robust features to securely as well as efficiently navigate through remote access use cases.
Why is ARCON | GRA a far better solution than ordinary remote access tools?
ARCON Global Remote Access
The reporting capability is highly advanced,
ensuring proper audits
A built for-purpose solution, offers a very intuitive administrative experience, improving business process agility
It offers a well-defined fine-grained control framework, improving business process outcomes and internal as well as operational effectiveness
An Ordinary Remote Access Tool
Does not provide an effective reporting functionality- hindering proper audits
Comes with clunky and cluttered GUI, hampering business and operational agility
Offers very tricky permissions management, especially while managing restricted acces