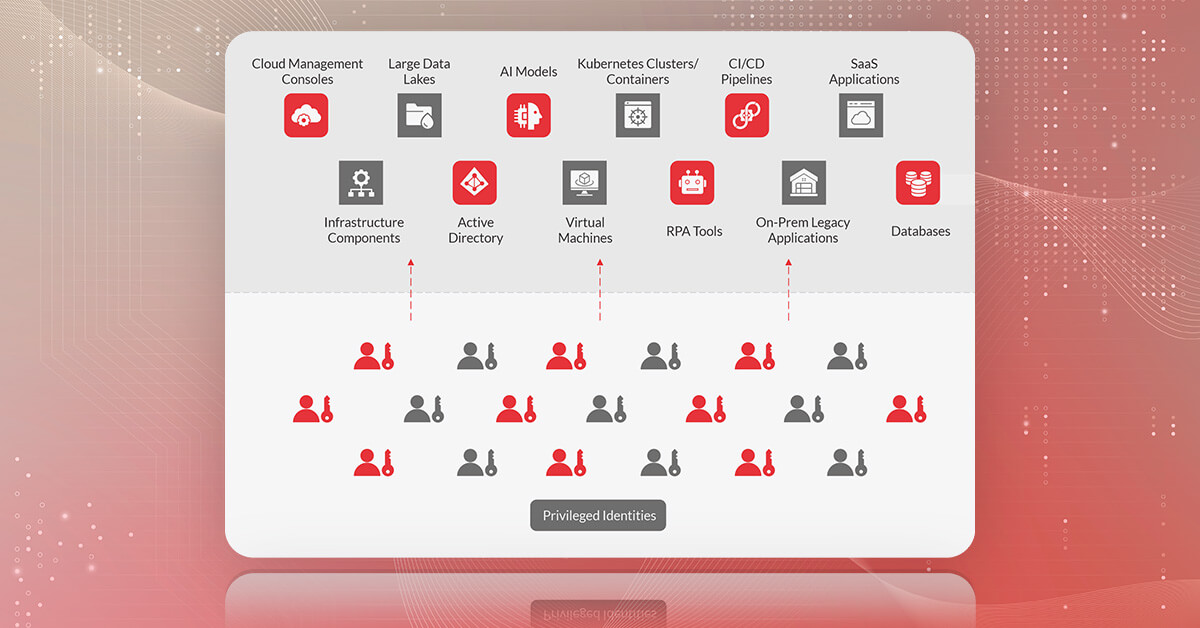
Modern Privileged Access Management (PAM) environments are not static but dynamic in terms of scope and requirements. Resultantly it leads to more complexities and challenges in managing privileged identities. It could lead to compromise of enterprise crown jewels.
Proactive PAM control mechanisms invariably provide security and risk management leaders with necessary safeguards to protect privileged identities – the keys to enterprise crown jewels.
What are these modern and trustworthy methods of securing enterprise crown jewels?
Download this whitepaper to learn more.