Are ROE, ROCE, ROA the Only Metrics for Investors?

Protecting Critical IT Assets Becomes More Important as Investors Look beyond Traditional Metrics For any publicly traded company or a private organization, creating long-term shareholder value remains a top priority. When a company consistently creates value, it’s easier to attract investments both for the organic or inorganic growth. Accordingly, the management always strive to improve […]
Will businesses stand the ‘risk’ of times?

All the top businesses today – Manufacturing& Distribution, Banking & Financial Services, Consumer Products & Services, Technology, Media & Communications, Healthcare & Life Sciences and Energy & Utilities – are expected to grow at a fast pace in the coming decade. However the evolution of these businesses comes at the cost of rising risks. Analyzing […]
Mapping Privileged Identity Management to an exotic travel

When I had started out in this industry, I had absolutely no clue of what Privileged Identity Management meant. In fact, not for a moment I thought it had something to do with security let alone cyber-security. I was deceived by the term ‘Privileged’ so much so that I started considering it be an elitist […]
10 steps to better manage Privileged Access
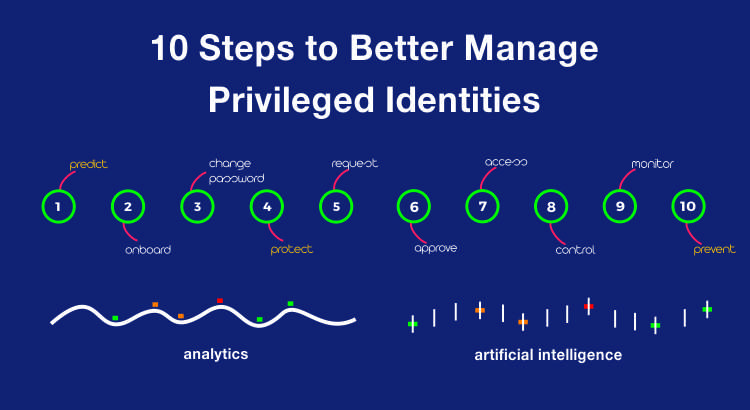
Andrew Dalglish, director of Circle Research, a UK based research firm recently said “The very people working in businesses can pose as the biggest threat to its security.” That’s a pretty huge statement to make come to think of it. Why would he say that when organizations across the world are taking the necessary precautions […]
Password Management Compliances across the World

In one of my previous roles as a test analyst, I was primarily responsible for constructing test cases for password management. At the time, I had devised a whole array of possible test cases for password management which included specifications on the length of the password, complexity of the password, frequency for changing password and […]
Privileged Thinking of the Cloud
Just as I went to collect my iPad this morning from the study room, something that was an integral part of my childhood grabbed my attention. This precious treasure was lying in one corner dusted and covered by a cloth which had torn. The treasure that I speak about was my best friend and is […]
Cybersecurity: Tackling the insider threat

Summary: In 2014, the world learned the hard way about data breaches due to insider threats. Learn why insider threats have become an increasing security risk and how to protect one’s self from it. In a world where data breaches are quickly becoming commonplace, even the best security technology in the world can’t help your […]
Data like water

is data like water? Data like water is an interesting analogy, It was only during one of my vacations that along a beach, i realized how the two are really similar and especially in the world of technology how data flow is akin to water flow. This paper tries to establish similarities, one’s ability to […]
Cloud Computing The business Perspective

Summary: The evolution of cloud computing over the past few years is potentially one of the major advances in the history of computing. Learn more about the various risks associated with cloud computing and how to choose the best cloud computing solution for your organization. The Business Perspective The evolution of cloud computing over the […]
Healthcare Debacle

Summary : Security breaches in healthcare are a major issue, but not enough attention is being paid to threats from the inside. A vast majority—92%—of healthcare IT decision-makers reported that their organizations are either somewhat or more vulnerable to insider threats, and 49% felt very or extremely vulnerable. Healthcare Debacle : – The insider security […]
