Andrew Dalglish, director of Circle Research, a UK based research firm recently said “The very people working in businesses can pose as the biggest threat to its security.” That’s a pretty huge statement to make come to think of it. Why would he say that when organizations across the world are taking the necessary precautions and spending billions on IT security? Well the answer to that is simple; most organizations are still focused on thoroughly securing their perimeter. Based on a survey by SpectorSoft, a pioneer in user activity monitoring and behavior analysis, a staggering 62% organizations saw a rise in insider attacks over 2014-2015. This means, although a majority of the organizations are aware of privileged access security and have security solutions in place, they have seen a rise in insider threats. Research firm Gartner has solved this mystery stating “Less than 5% of the organizations were tracking and reviewing privileged activity in 2015. The remaining are at best controlling access and logging when, where and by whom privileged access has taken place but not WHAT actually is done.”
Maybe the reason for this is lack of knowledge or awareness amongst the employees about the importance of privileged security. This was validated by Ernst and Young in their 2015 Global Information Security Survey where they identified careless or unaware employees to be one of the top two vulnerabilities exposing organizations to cyber-attacks. And if this is left unaddressed, then as per Gartner, by 2018, privileged access will be responsible for up to 60% of insider misuse and data theft incidents.
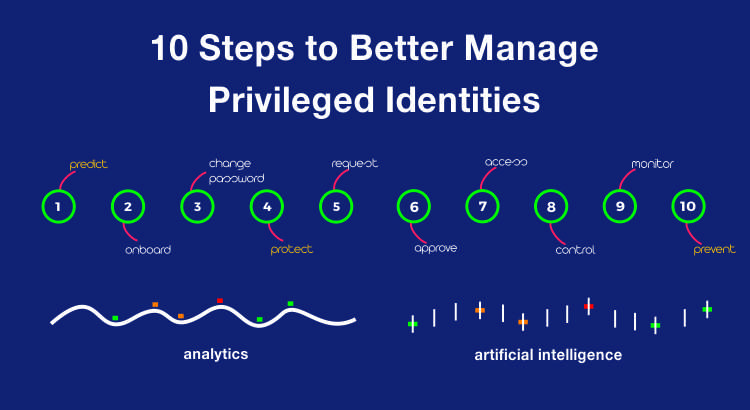
So as responsible cyber security specialists, we felt the need to create awareness on this matter. That is why the ARCON team has meticulously devised a list of 10 steps on how you can better manage Privileged Access.
1. Predict: As a first step to your privileged identity program, you must plan and evaluate all your user entries who needs to access your environment, e.g. Contractors, temporary staff, offshore employees, employees etc. As a best practice, these privileged users should be recorded and accounted for.
2. Onboard: Onboard privileged accounts including shared accounts, named entities, service accounts to the PAM solution. This also means the privileged accounts should be assigned an ownership in an indirect manner i.e. on a functional level and not an individual level. This way, your IT system is not exposed to orphan accounts whenever an individual moves out of your organization thereby securing a vulnerability.
3. Change Password: Plan a password rotation program to plan all privileged accounts in the environment are protected by your password management policies. This is best done using an SAPM tool that allows for automatic password generation and change.
4. Protect: Ensure passwords are managed in the electronic password vault which is highly available and tamper proof in nature. This allows for passwords to be stored in a highly secure electronic vault offering several layers of protection and creating a virtual fortress thereby.
5. Request: Design a workflow for password or access usage to control password access to all relevant stakeholders within your IT environment. Manually designing a workflow can be fragile and hence it is advisable to implement solutions worthy of automating processes and enforcing controls.
6. Approve: It’s important to designate competent individuals to ensure right approvals are defined for each access request. This must be managed by a solution with right audit trails to track such approvals. This will also ensure least privilege principle limiting the scope of any privileged account giving them minimum rights for performing exactly the specific task which the respective account is needed to perform and nothing more.
7. Access: Next step is to define and extend governance controls to your access rule list linked to individual and critical accounts. By doing this, you are meeting your organization’s compliance requirements by periodically reviewing and validating number of privileged users, who the privileged users are, their access rights and what activities they perform under the guise of a privileged user.
8. Control: Enforce strict policies in line with your security policies to control password release function, password usage function for all your IT equipment.
9. Monitor:Establish policies in place to log, monitor, report and analyze privileged user sessions/activity. It is highly recommended to monitor and review privileged activity real-time by implementing a live dashboard monitoring tool. Also, it is best practice to periodically review session logs and not just when an incident needs to be investigated as this helps analyze privileged user behavior to critical systems.
10. Prevent:The next and most vital level of privileged access management is to implement preventive access control policies to granularly control critical activities of IT administrators and super-users. This ensures that super-users do not have more privileges than are needed and essentially helps split up required privileges among administrators depending on their specific task. Additionally, it ensures a separation of access privileges between the administrators, developers, testers and operators on your IT systems.
The above are as we have coined it the 10 golden steps of Privileged Access Management / Privileged Identity Management. Our team’s extensive experience and expertise to analyze the IT systems have guided us in developing these steps. Our consultative approach on these matters in addition to our solutions have also primarily led to our clients follow these best practices.We advise the same approach to many of our existing clients, potential clients and partners that we have come across on several events and conferences that ARCON has been a part of. And we are certain that following the above will go a long way in providing what we call ‘absolute protection’ to your organization.
ARCON provides state-of-the-art technology aimed at mitigating information systems related risks thereby enabling organizations to comply with Governance, Risk Management and Compliance (GRC) requirements. The company, in particular, is known for its unique Privileged Identity Management/Privileged Access Management solution, which helps deter the misuse of ‘privileged identities’.
Learn more about us at www.arconnet.com