Seamlessly Scale the Privileged Access Management Environment with ARCON | PAM SaaS

Overview The Privileged Access Management (PAM) space is growing at a brisk pace. There is a rising demand for PAM solutions to address many critical enterprises’ use cases that include cloud access governance, DevOps use cases, shared accounts, and non-human identities interacting with RPAs. In one of the “trend” reports by Forrester in 2021, the […]
Zero Trust Architecture: Why is it Unshakable?
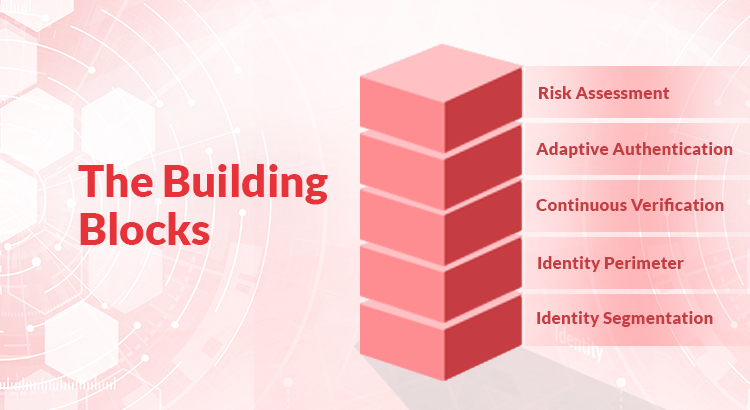
An Overview New technologies and IT infrastructure modernization have extended the boundaries of identity. And these ever-expanding IT boundaries pose a mighty challenge for information security heads. The challenge is not simply to maintain strict identity controls. The bigger challenge is that these ‘trusted identities’ are dispersed in decentralized IT environments. There is a growing […]
Implementing Multi-factor Authentication (MFA) to Protect Data and Sensitive Information

About authentication and passwords “Treat your Passwords like your toothbrush. Don’t let anyone else use it and get a new one every six months”. – Clifford Stoll, American astronomer, and author Yes, passwords are among the most vulnerable IT assets. Password breach or credentials breach (User identity and password) are among the most common causes […]
KuppingerCole Leadership Compass for Privileged Access Management

Yet another feather in the cap! ARCON has been named an “Overall Leader” in the 2022 KuppingerCole Leadership Compass for Privileged Access Management report, written by Paul Fisher, lead analyst of KuppingerCole Analysts AG. The phenomenal run for ARCON as a business organization that focuses on protecting digital identities and vaults (for securing secrets) continues, […]
The Journey of ARCON: Upwards and Onwards

ARCON ends the year 2022 on a high note ARCON believes in consistency, and consistency is the key ingredient to success. This is exactly what happened in 2022, another eventful year, when ARCON continued to make rapid progress on its global expansion plans, win the customers’ accolades, and win their trust even as our flagship […]
How to Secure New IT boundaries amid the Adoption of Hybrid Data Centers and Multi-cloud Environments?
Overview “Change is inevitable” and “Evolution is never-ending”! This adage particularly holds true for IT infrastructure and operations. Indeed, in an extremely vast IT setup, new IT boundaries (and new IT challenges) are emerging as organizations model their data center architecture in hybrid (partially on-prem data centers, partly in the cloud) or multi-cloud environments for […]
Protecting Non-human Identities for a Holistic Identity and Access Management Framework

Overview “Automation” is the new-age mantra in information technology management. From large enterprises to mid-size organizations, IT infrastructure and operations teams are increasingly implementing process automations. The two major reasons behind the growing acceptance of process automation are higher IT efficiencies leading to better operational outcomes and a reduced number of man-hours spent on mundane […]
An Examination of Three Incidents in Which Privileged Access Management Could Have Prevented a Data Breach

Overview In an increasingly digitized, decentralized, and distributed IT environment, the security of data can only be possible when organizations adopt an identity-first security approach. Indeed, the biggest cybersecurity threats lie with cybercriminals and malicious insiders who can gain easy access to critical systems and applications to compromise data and information. Such attacks become more […]
Leverage ARCON | Enterprise Vault to Automate Password Management Process

The Context Today, enterprise’s identity and access management environments are continuously facing threats of password misuse. Application service accounts that use privileged credentials to run scheduled automated tasks are no exception. Indeed, with the proliferation of service application accounts in an increasingly heterogeneous IT environment, the underlying applications in any IT environment are continuously facing […]
Unmatched Attributes that Set ARCON | Privileged Access Management Solution Apart from Others

Overview Privileged Access Management (PAM) solution is an absolute must for any organization looking to ensure data integrity and security while also fulfilling compliance requirements. A robust PAM solution offers all-around capabilities such as just-in-time access to target devices, privileged access threat analytics, session management and session recording, privileged elevation and delegation management (PEDM), and […]
