Secure Passwords, Save your Digital Assets

Who can forget the infamous data breach incident of one of the popular file hosting service providers where more than 60 million users’ email addresses and passwords got affected? An employee just reused a password at work and that was the mistake. The password was broken through to steal the valuable records of the organization. […]
Role of PAM in meeting Regulatory Compliance
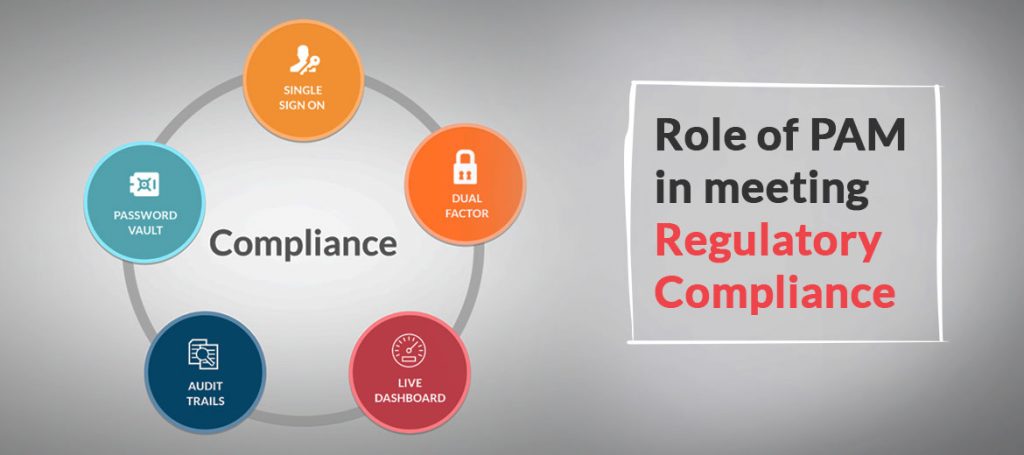
Facebook could face penalties worth in billions under GDPR (General Data Protection Act) compliance act for not following the basic policies. It happened because more than 50 million accounts were compromised due to some negligence from this social media giant. As detected during the end of September, 2018, Facebook unveiled that a particular vulnerability in […]
How to mitigate misuse of Privileged Accounts

Misuse of privileged accounts is one of the burning threats for enterprises today. The detection process is time-consuming. Even if the organizations try to calculate the amount of loss incurred from these threats, it is never possible to get the exact figures because the overall damage is irrevocable – both financial and reputation-wise. 1. Controlling […]
