ARCON and KuppingerCole recently co-hosted a webinar to discuss and analyze some important cloud access management strategies to enhance cloud security. On May 21st, 2024, Paul Fisher, Lead Analyst, KuppingerCole Analysts AG and Harshavardhan Lale, Vice President of Business Development, ARCON turned their attention towards the role of Cloud Infrastructure and Entitlement Management (CIEM) tools in building a robust cloud-first journey.
In this webinar, both speakers covered the major risks emanating from managing workforce in multi-cloud platforms, what are the emerging trends, and how CIEM tools can help to strategize cloud security posture.
During the first half of the webinar, Paul Fisher from KuppingerCole highlighted how privileged access management can strategize cloud access management in enterprises. Below are the key takeaways from the first half of the session:
-
- Enterprises seek many business benefits from cloud adoption. The major ones among them are rapid delivery, uninterrupted user experience, convenience, data management and overall IT security. End-users and IT administrators find a multi-cloud environment extremely beneficial for remote working, multi-location access and collaboration among the workforces.
-
- Future of Jobs report 2023 by World Economic Forum predicts that 76.6% organizations are going to adopt cloud computing between 2023 – 2027. As a result, we observe that the number of identities in cloud environments is expanding uncontrollably. There are multiple reasons behind it – non-human identities outnumber human identities and there are identities from third parties/ supply chain. Moreover, there is integration of clouds, Apps, and resources. There are frequent changes of application as well.
-
- Identity Access for Data in Business has evolved dramatically. KuppingerCole has identified 7 types of identities that are dominant in a typical IT infrastructure. These are IT administrators, machine identities, end users, third-party users, developers, endpoints, and customer identities. The data includes files, Apps, workloads, code, admin accounts, privileged data, privileged credentials, DBs, etc.
-
- The major identity challenges identified by Paul are over-privileged entitlements, privileged access controls, cumbersome credential management, weak identity threat detection, reliance on vaults and passwords, inefficient or zero entitlement management.
-
- Among the IT security priorities marked by KuppingerCole is making Zero Trust a reality and security goal by 41.2% and Implementing MFA by 35.3%. Organizations securing, limiting, and enforcing person and non-person entities’ access to Data Applications Assets & Services (DAAS).
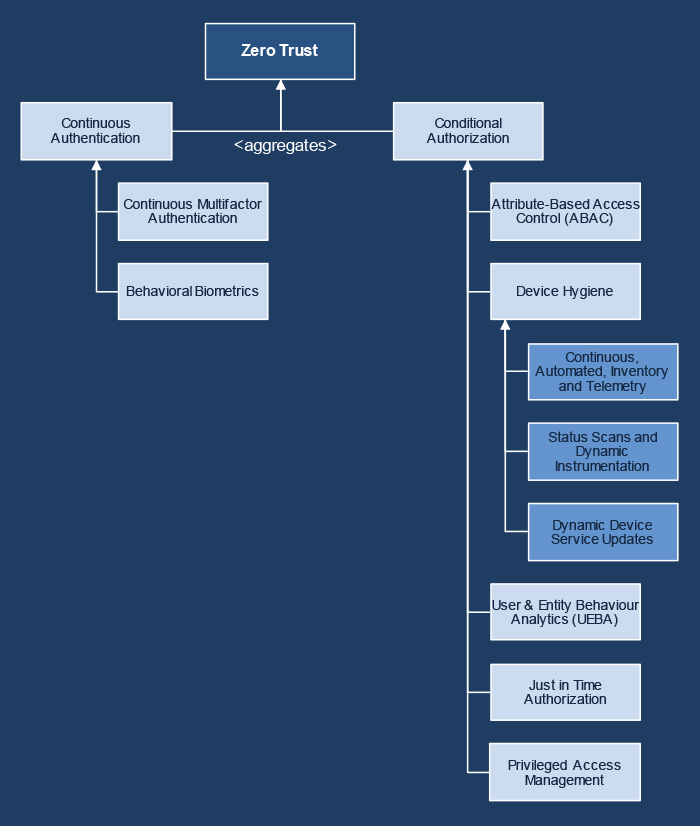
- Among the IT security priorities marked by KuppingerCole is making Zero Trust a reality and security goal by 41.2% and Implementing MFA by 35.3%. Organizations securing, limiting, and enforcing person and non-person entities’ access to Data Applications Assets & Services (DAAS).
-
- Organizations need the ability to continuously authenticate, authorize, and monitor activity patterns to govern users’ access and privileges while protecting and securing all interactions.
-
- CIEM helps organizations to manage and secure their identities and access entitlements across cloud environments. CIEM solutions focus on minimizing risks associated with excessive permissions, misconfigurations, and identity sprawl in cloud platforms.
-
- CIEM solutions continuously monitor permissions and roles to adapt to changes in the cloud environment, ensuring that security and compliance are mandated.
-
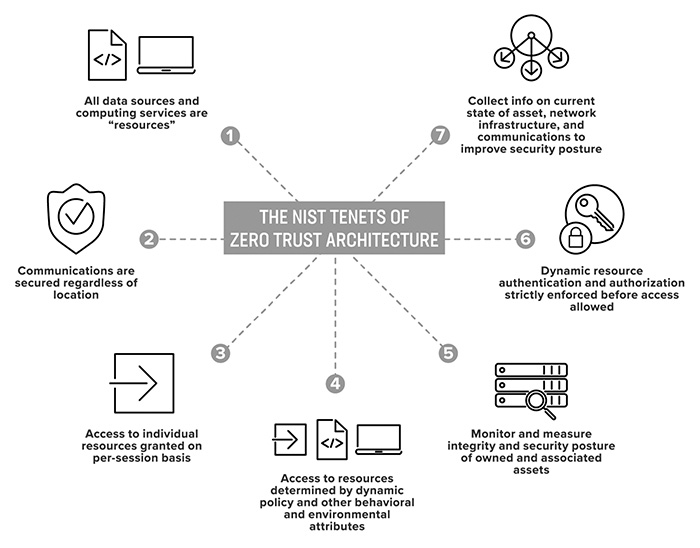
- Lastly, KuppingerCole highlighted the NIST tenets of Zero trust architecture research that bears credibility in the IT security market globally.
In the latter half of the webinar, Harshavardhan Lale from ARCON discussed how cloud access challenges can be managed strategically and govern multiple user IDs in an ever-expanding multi-cloud environment and explained how ARCON’s Cloud Governance solution can help to address the challenges. The key takeaways from his session:
-
- ARCON started by sharing the concept of Privileged Access Management (PAM) concisely. It provides administrators with the functionality, automation and reporting they need to manage privileged accounts, handles access permissions based on roles and policies, controls administrative access, limits access to specific functions and resources and more.
-
- In continuation of Paul’s discussion about proliferation of identities, Harsh added that identities are the weakest link to compromise enterprise information assets. It includes human (business) identities, machine identities, privileged identities, BOT identities, APIs etc. Eventually, all the identities are converged into digital identities.
-
- that are provisioned/ deprovisioned/ re-provisioned to manage and control the activities.
-
- Enterprises can secure their cloud environment by deploying PAM through which they can onboard cloud infrastructure end users, make them access-ready, monitor the access and rotate credentials/ keys. This way, they can meet compliance requirements.
-
- ARCON has made onboarding quite simple through different directories for AWS, Azure, or GCP through Auto-onboarding feature. With this, IAM users can auto onboard in SaaS environment, Windows, Linux and RDS (database) users can auto onboard in IaaS and PaaS environments. This automated task can happen in every cloud platform like AWS, Azure or GCP with any requirement of an IT administrator.
-
- The methods we use to auto onboard are SSH/ PEM keys, AWS session manager using STS or even Hardened server. All are applicable to Azure, AWS or GCP platforms.
-
- The access to cloud service providers must be monitored and done in separate ways for different service providers. ARCON secure all these accesses shown here:
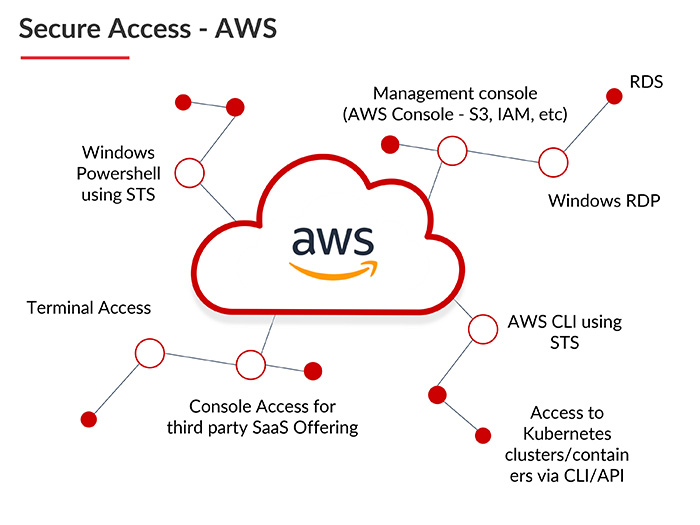
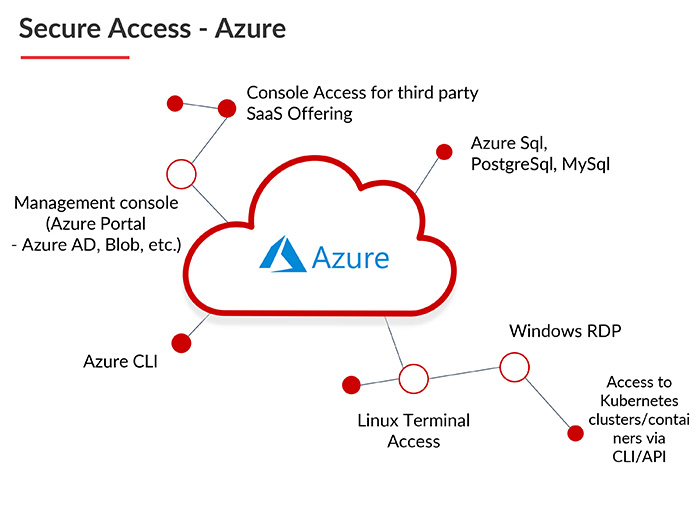
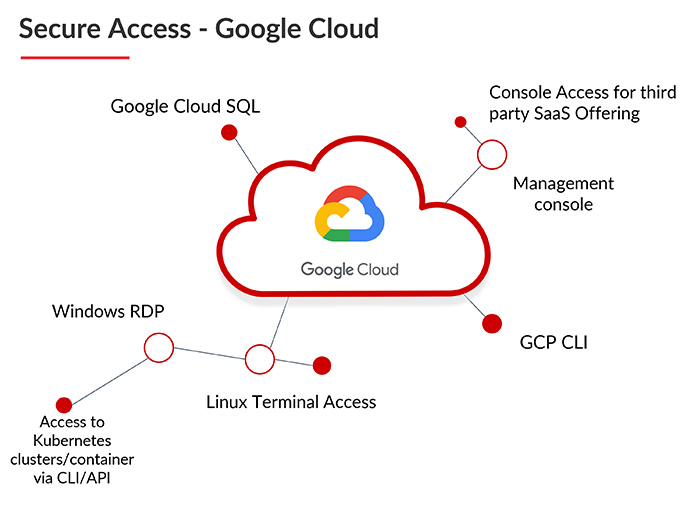
- The access to cloud service providers must be monitored and done in separate ways for different service providers. ARCON secure all these accesses shown here:
-
- It is not just the infrastructure but also the Cloud Apps that are managed by ARCON. For example, GitHub, Salesforce, G-suite, Office 365, etc. How do you really.
-
- manage to secure access to these cloud Apps? It is with the help of ARCON | PAM, enterprises can take complete control of the access management process.
-
- Password Management is another key security element in cloud environments. ARCON does password management for databases, EC2 instances (Windows & Linux), IAM User (Access Key & Secret Key) and IAM console user that are applicable to AWS, Azure or GCP.
-
- Lastly, Harsh discussed the complexities of hybrid cloud environment where some of the workloads are on AWS, some on Azure and some on Google Cloud. In this situation if the administrator wants a single window view of what is happening on which platform, CIEM is the answer. However, the challenge with CIEM solution is – how do you manage the entitlements? ARCON | PAM’s CIEM component strengthens the security fabric on cloud as administrators can define the policies and permissions for distinct entities wanting to access files, workloads, databases, management consoles, services, servers, containers, and many other cloud resources. It can even control misuse of over entitlements in the cloud environment that could invite unprecedented IT threats.
Conclusion
The webinar concluded with a quick overview of ARCON’s business portfolio. Before the final wrap up, Paul and Harsh discussed webinar poll results. The poll question “Do you currently have any means to control over-privileged identities?” received response from 78% attendants stating “Yes – PAM”, which indicates preference for a comprehensive PAM solution in enterprises worldwide. Almost 77% respondents in the second poll question “What do you understand by Zero Trust Network Architecture?” said that “It’s complicated to implement.” Indeed, both Paul and Harsh agreed to the fact that building Zero Trust Security posture is challenging if we wish to ensure IT security and IT efficiency simultaneously.

