PAM, People and Processes
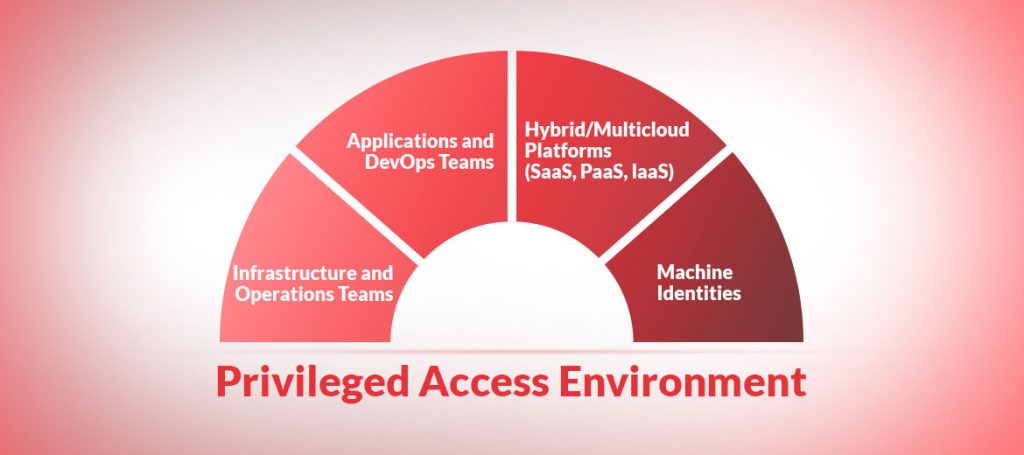
That the effectiveness of a PAM tool is only as good as the organization’s outline around its PAM practice was never so true as today. Indeed, while integrations and automation of PAM tasks remain at the core, managing people, and processes are important too. All the automation initiatives can be undermined without proper controls around […]
