That the effectiveness of a PAM tool is only as good as the organization’s outline around its PAM practice was never so true as today. Indeed, while integrations and automation of PAM tasks remain at the core, managing people, and processes are important too. All the automation initiatives can be undermined without proper controls around people and processes.
PAM implementation: The emerging contexts
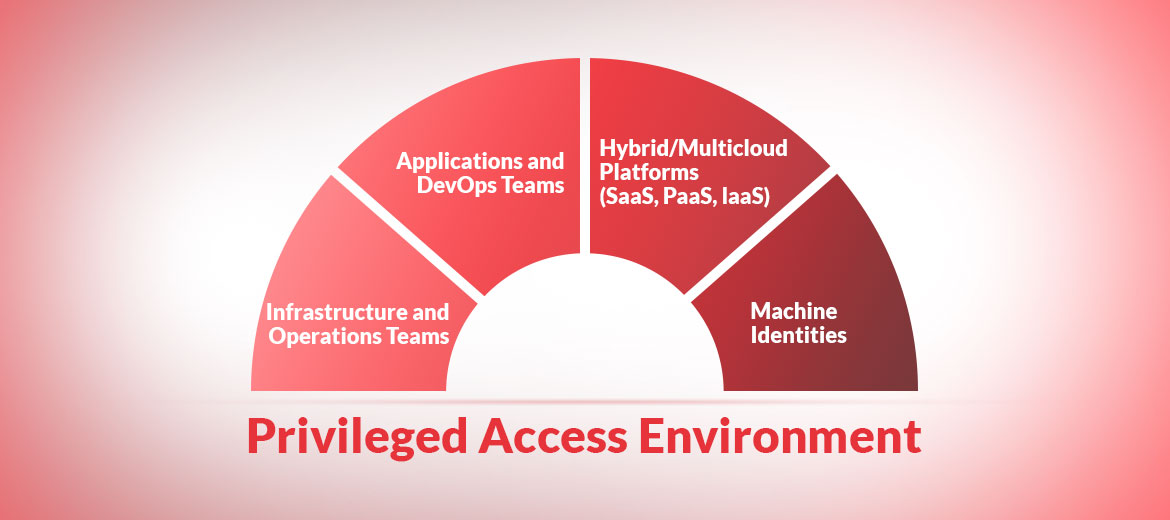
There is a sharp increase in the number of PAM use-cases and the complexities around those use-cases. There was a time when PAM implementation was the requirement for securing and controlling IT operations and infrastructure access environments. On-prem datacentre was the only perimeter to control privileged identities.
But now with hybrid and remote work environments, multi-cloud platforms (IaaS, PaaS and SaaS), including privileged access for DevOps environments and non-human identities—the contexts are fast changing. And in many instances, new contexts are emerging as well.
Resultantly, today’s mid-scale and large organization have a higher number of privileged identities to manage. There are a higher number of PAM functional domains. As a result, there tends to be a greater number of roles and responsibilities. Consequently, it leads to an increasing number of users, user-groups, services and service groups.
An evolved and mature PAM, capable of supporting high-velocity PAM requirements can support these emerging and changing use-cases.
Under emerging contexts, the effectiveness, however, will also depend on how the users will be administered, and the rules enforced. In other words, a sloppy organization around people and policies can derail the entire PAM set-up.
Managing people and processes: The foremost requirement for a successful PAM implementation
In any IAM environment that includes PAM, there is a set of basic dos and don’ts. And implementation of this set of rules ensures stable and agile PAM environments. Correspondingly, non-implementation can lead to security loopholes and a data breach.
For instance, consider an on-prem datacentre. With the emergence of new use-cases as discussed above, enterprises have built micro-perimeters outside the traditional realm of a datacentre. The digital identities that were once segmented inside the on-prem datacentre are now micro-segmented to accomplish privileged tasks.
Against this backdrop, complete discovery of all privileged access along with mapping and tracking of all users and accounts is necessary for all organizations. There must be an unambiguous set of comprehensive governance policies that are well-defined, clearly itemized and enforceable.
The efficacy of PAM will never reach the desired level if:
- Organizations’ wide-ranging privileged access environments are operated in silos without centralized governance
- There is no distinction between authorization and authentication
- No pre-defined policies around people (role, risk, purpose, access rules)
- No pre-defined policies around processes (Password policies, MFA policies, workflow matrix, itemization of privileged tasks)
The bottom-line
To secure and control privileged access, organizations must set up comprehensive policies around people and processes.