Securing Enterprise Data – The Soul of any Business

In a continuously evolving technological landscape, global organizations are coming across new challenges to store and protect a huge amount of business data generated every day. While data being the core of any business, it plays the most important role in maintaining business continuity in any industry. While many organizations go all the way to […]
Security Essentials in Managed Service Environment

A rundown on webinar hosted by ARCON and KuppingerCole With a mission of spreading information security awareness and educating global folk about the security risks involved in uncontrolled and unmonitored privileged activities and their remedies, ARCON has become a global thought leader in the IT risk-preventive technology space. We participate in the global events, showcase […]
ARCON Travels the World to Spread Awareness on Privileged Access Security

As the latter half of year commences, ARCON would like to take you back in the last six months in which the company has been busy with global thought leadership summits and round-table conferences. ARCON would like to recollect and highlight some glorious moments of our journey, wherein it shared in-depth knowledge of Information Security […]
Data Security in Managed Service Environment

Today, it is a big challenge for organizations to secure their Information assets from persistent cyber threats from both external and internal malefactors, arising mainly due to distributed nature of IT infrastructure. Take for instance, the Managed Service Provider (MSP) model. MSP is a cost-effective alternative for organizations to ensure business continuity with limited workforce […]
Secure Data before it Goes Up for Sale

Data – the lifeline of any business organization, is under grave risk today due to numerous cyber security threats. Along with the rising number of threats, the nature of attacks is also getting sophisticated day by day. The cyber crooks are adopting advanced hacking techniques to steal sensitive data. Phishing, Ransomware, DDoS (Distributed Denial of […]
Spot your malicious insider(s) with ARCON | UBA

Recently, a Government organization from Healthcare industry in APAC region revealed that almost 14,000 health records were leaked online because of a malicious insider. The organization never thought that they could lose their sensitive health records to someone trustworthy (apparently) in unbelievably nasty way. Couple of months back this incident shook the cyber world and […]
Passwords are your safety doors: Lock your assets or leak them

In the beginning of 2019, more than 773 million email IDs and 21 million passwords were hacked which is claimed to be the biggest hacks of this year (so far). Australian researcher Troy Hunt discovered this and mentioned it in his website “troyhunt.com”. This incident threw a fresh question to us whether we are digitally […]
Secure sensitive data with robust Privilege Account Lifecycle Management
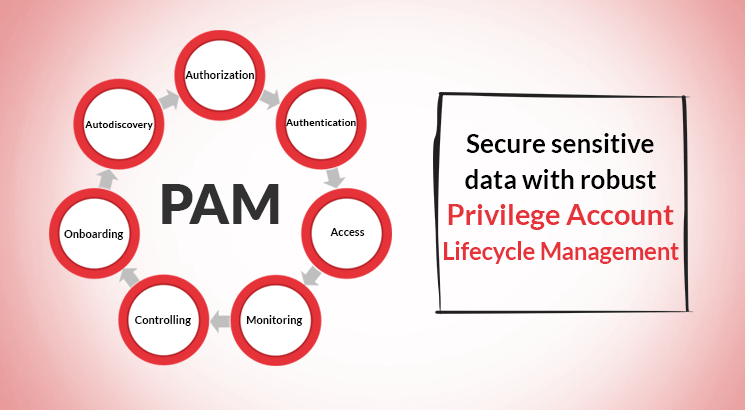
Probably there are more number of digital identities today than the human population on this planet. Indeed, digital identities have spiralled as our modern day economy is propelled by cloud computing, artificial intelligence, and big data analytics among several other disruptive technology innovations. A growing number of digital identities, however, has opened up the gates […]
10 Best Practices for PAM solution
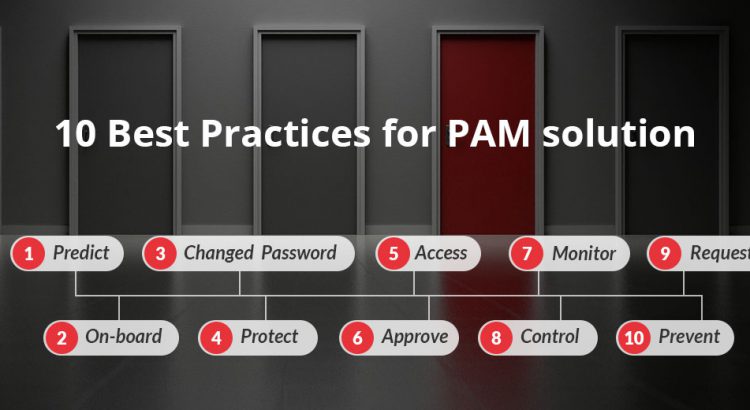
Privileged Access Management (PAM) is one of the most discussed area of today’s cyber security arena. With the increased number of alarming data breach scenarios worldwide, it is very obvious that PAM solution would shield the organizations from any threats arising from unmonitored accounts or poor access control system. Here is a brief account of […]
IT Central Station Users Share What They Love about ARCON

Over the last few months, the team at IT Central Station reached out to ARCON Privileged Access Management customers with one goal: to find out what they really think about their experiences with ARCON. As the leading user review platform for enterprise technology solutions, we are always on the hunt for user feedback that can […]
