Privileged Access Management (PAM) is one of the most discussed area of today’s cyber security arena. With the increased number of alarming data breach scenarios worldwide, it is very obvious that PAM solution would shield the organizations from any threats arising from unmonitored accounts or poor access control system. Here is a brief account of few practices that could enrich Privileged Access Management (PAM) to the next best level of robustness.
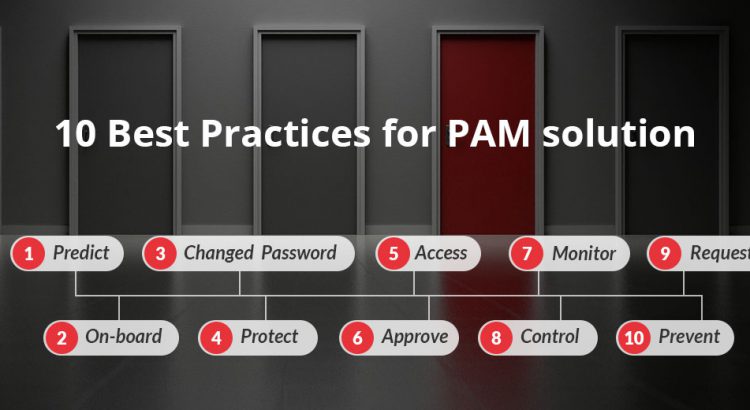
Predict: Adequate and channelized planning and evaluation of all user identities who access or require to access the accounts.
On-board: On-board all the major Privileged accounts including the shared accounts, named entities, service accounts to the PAM solution. At the same time, the number of privileged accounts should be bare minimum – exactly which is required to perform tasks.
Changed Password: Strategic planning of a proper password creation and rotation ensures all privileged accounts in the network are protected with password management policies. In addition, simple and lucid password characters that are easily predictable should be avoided.
Protect: Passwords are managed in the electronic password vault which is highly available and tamper proof in nature. Since its very difficult to establish a manual control over password change process, thus password vault automatically generates dynamic passwords for several devices at one go.
Request: Design a work-flow for access control to all relevant stakeholders within the enterprise IT environment.
Approve: It is very crucial to designate someone competent to make sure that correct approvals are defined for each and every access request to the privileged accounts. This must be managed by a solution with right audit trails to track such approvals.
Access: Defining access rules linked to the critical privileged accounts and individuals are the next important thing to ensure strict vigilance.
Control: Stringency in the security policies can control password release function and password usage function for all equipment in the system.
Monitor: Restriction of time and duration of access hours is very important to monitor user activities. Also, service, application, software accounts that are allowed remote interactions should be under security radar round the clock.
Prevent: Lastly, Privileged Access Management (PAM) program should have preventive access control policies to stop unauthorized accesses and granularly control critical activities of the IT/ system administrators.
ARCON is a leading enterprise risk control solutions provider, specializing in risk-predictive technologies. ARCON | User Behaviour Analytics enables to monitor end-user activities in real time. ARCON | Privileged Access Management reinforces access control and mitigates data breach threats. ARCON | Secure Compliance Management is a vulnerability assessment tool.