Probably there are more number of digital identities today than the human population on this planet. Indeed, digital identities have spiralled as our modern day economy is propelled by cloud computing, artificial intelligence, and big data analytics among several other disruptive technology innovations.
A growing number of digital identities, however, has opened up the gates for cybercriminals. As digital identities are identifications used for connections or transactions on network and internet, hackers and malicious corporate insiders are always on a lookout to abuse them for gaining unauthorized access targeting personal and critical information assets.
One of the biggest sources of data breach are privileged identities and accounts.These identities and accounts are extremely vulnerable to abuse as they provide access to critical systems and sensitive information. These accounts are found everywhere. On premises data centers, on cloud where organizations manage hundreds of applications and databases, network assets (routers firewalls) including operational technologies (SCADA, ICS).
In a typical use case scenario, malicious insiders and compromised third party elements can take advantage when organizations pay scant attention to the rising number of privileged users in an enterprise IT environment.
Unaccounted surge in the number of endpoints and privileged accounts, consequently, provides potential ways to the compromised insiders and malicious third parties to gain access to enterprise networks and critical systems.
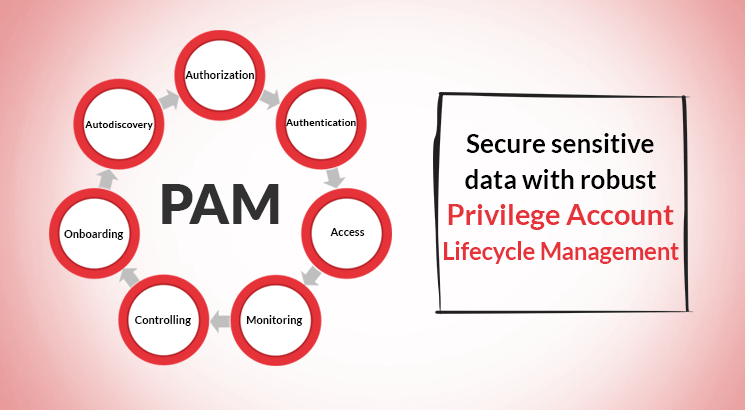
The threat is compounded by the fact that that these privileged accounts are often created in a ad-hoc manner. In this backdrop, there is a complete mismanagement of privileges. Absence of authorization, authentication, audit trails, monitoring and controlling of privileges puts the entire IT infrastructure under grave risk. A modern day enterprise requires a centralized and role based privileged access management that automates the entitlement and validation process including privileged access and services. These privileged access practices help in managing the lifecycle of privileged identities.
Think about how difficult would it be for the IT security team to keep a track on privileged account activities when there is no proper mechanism in place to manage and monitor privileged accounts?
Privileged Access Management offers your IT security team a sure-fire way to reinforce the security posture. It enables them to seamlessly manage the Privilege Account Lifecycle by.
1. From centrally administering and defining rule-based access policy to auto-onboarding of privileged users, your
enterprise privileged data security will never be compromised as every access will be after thorough validation
2. Auto-discovery of all privileged accounts and devices to ensure every activity is documented and no privilege
account is abused
3. No more emails and tedious documentations. Gain operational efficiency. Workflow matrix will enable to
configure approval process for user/user groups and service groups
4. Audit trails and customized reports of every privileged access to meet regulatory standards
ARCON is a leading enterprise risk control solutions provider, specializing in risk-predictive technologies. ARCON | User Behaviour Analytics enables to monitor end-user activities in real time. ARCON | Privileged Access Management reinforces access control and mitigates data breach threats. ARCON | Secure Compliance Management is a vulnerability assessment tool.