Digitalization, GDP Growth and IT security threat
Information Security has taken a center-stage in the nation-building process. It significantly influences the annual GDP of every nation.
While digitalization is adopted rapidly, the business data flows unceasingly from one device to another, from one IT environment to another. Data generation, processing and analysis of the same builds the foundation for any organization. This is a growth enabler for businesses and organizations. Big data helps businesses and organizations to understand the trends and patterns leading to innovation and experimentation. That in turn contributes to the nation’s economic growth.
Now, if this sea of information that is generated, shared and stored every minute is not protected from cyber criminals, organizations and businesses might suffer irreparable loss in terms of both finances and reputation. This in turn can impact the national GDP.
While explaining the role of the internet in GDP growth, McKinsey, in one of its reports, has stated that the internet contributes to 3.5% of global GDP, which is definitely a respectable portion. Moreover, the wave of digitalization has impacted significantly on the wealth and standard of people’s living.
And it is not just the IT or e-commerce industry, the role of cybersecurity has become critical for manufacturing, pharmaceuticals, financial services among many other traditional industries. It is estimated that around two-thirds of the economic value created over the internet is from traditional industries.
Gross Domestic Product (GDP) functions as a comprehensive scorecard of a given country’s economic health, hence, the role of IT security cannot be ignored.
Who are the threats to IT infrastructure?
Compromised Corporate Insiders: The insiders are privy to confidential information and business sensitive data, sometimes with privileges to access critical systems.
Unethical Third-Parties: Third-party vendors/consultants control organization’s data indirectly – they have access to systems and applications for maintenance and storage purposes that can be compromised.
Organized Cybercriminals: Call them hackers, “hacktivists”, or by any other terminology – the objective is to harm businesses and organizations by stealing/encrypting/or misusing the data for financial gains.
What Measures can be taken to secure Information Assets?
IT Security plays a pivotal role in securing global enterprises from cyber threats. At the same time, it ensures that business continuity is unhindered, and the graph of GDP remains stable.
At the macro level, the national-level cyber-defense strategies help enterprises to reinforce their IT ecosystem by providing
- Laws to define what constitutes a cyber-crime
- Incident Response and Disaster Management Agencies to thwart and detect cyber-attacks
- Cyber-security Awareness Programs at the national level
Besides,
- Every organization from both traditional and unconventional industry should educate and train the workforce on safe IT practices
- Regardless of geographical location, every organization from every country should cooperate and communicate with each other to stay updated with safe IT practices.
- There should not be any alternative to following standard global regulatory compliances. Every industry from every region needs to follow the applicable mandates to ensure smooth IT operations.
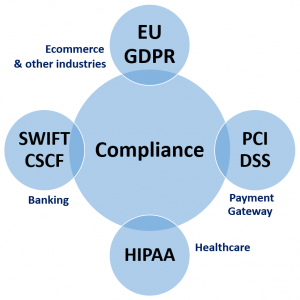
- And of course at the micro level, businesses and organizations should assess the critical IT infrastructure, its vulnerabilities and how the data can be best managed securely in a large ever-growing IT infrastructure.
- Endpoint security, Identity and Access Management, Vulnerability Assessment tools, Privileged Access Controls are some of the critical safeguards that can strengthen the IT perimeter.
Conclusion
Human capital, technology and disciplinary law tops the list of factors that contribute to GDP growth across the world. And the technology part is arguably inclined towards new-age digital transformation. That’s why Securing IT processes and operations is at the core of nation-building.