Identity Governance: How to keep the House in Order?

Probably the most convoluted IT practices of all, the Identity Management and Governance is always vulnerable to a security gap. After all, controlling a vast expanse that extends beyond the traditional realm of a datacenter demands careful planning. While spiraling cost issues and inadequate resources often undermine the identity governance approach, the inherent shortcomings are […]
PAM, People and Processes
That the effectiveness of a PAM tool is only as good as the organization’s outline around its PAM practice was never so true as today. Indeed, while integrations and automation of PAM tasks remain at the core, managing people, and processes are important too. All the automation initiatives can be undermined without proper controls around […]
How to Ensure Robust Compliance and IT Audits?

Enterprise IT vulnerability assessment in a timely manner is one of the basic requirements to ensure a robust IT security framework. And IT audits and compliance help the IT Risk Management and Compliance team to identify and assess underlying IT vulnerabilities. Yet, far too often organizations commit a mistake of manually conducting compliance and audit […]
Why Just-In-Time Privilege Elevation?

One disconcerting aspect in privileged access management (PAM) is that organizations are often not completely accustomed to widespread risks. Even if the PAM tools are in place, the fundamental principles sometimes could take a backseat. For instance, noncompliance to the ‘Least Privilege’ principle due to the absence of Just-in-time (JIT) privilege elevation approach. Scenario 1: […]
Digital Transformation and Pitfalls

A seamless digital transformation tops any modern organizations’ mid to long-term vision. The benefits are too many. Moving away from legacy business approach to digital business approach enhances business agility and efficiency. The Return on Investments (ROI) might increase as digital technologies enable to market products and services faster at lower costs. Nevertheless, it is […]
Why Contextual Authentication?

Contextual authentication is gaining more and more prominence in the overall cyber threat and IT frauds prevention landscape. The risk stemming from IT fraudsters needs attention as the ‘bad actors’ often outsmart ‘good actors’ in the cyber warfare. The bad actors have an uncanny knack to deceive the security controls in place. Although organizations and […]
Endpoint Security: A tactical priority

Endpoint security is as important as identity governance and access management Information security receives significant focus these days. Amid increase in cyber-attacks, notably on endpoints, there is an urgent need to build a secure and reliable IT framework. Identity and Access Management (IAM) and cloud identity governance, several studies show, receive maximum IT security spending […]
Endpoint Security Revisited

Endpoint Security dominates the IT security concerns lately. Endpoint access anomalies—never taken into account before— surfaced all of a sudden due to the pandemic. The WFH scenario took everyone completely by surprise. Subsequently, protecting corporate data became a little more difficult. The end-users – out of the restricted on-prem periphery – use personal devices and […]
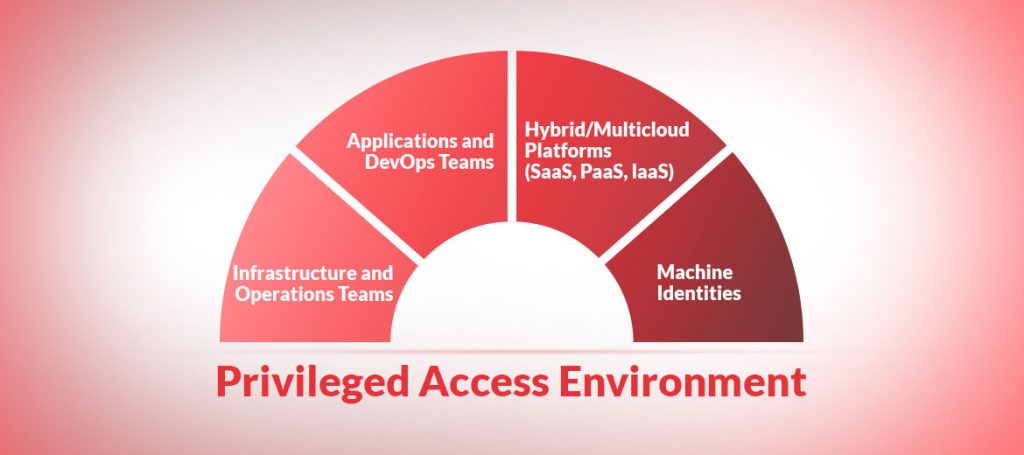
Privileged Access Environment: How to avoid chaos?

A privileged access environment often reminds the IT community of a maze. In both instances, chances are high to get lost in the way. Consider a maze, when we enter it, we are confident to make it. However, with every move, and every turn we take, we invariably start to lose our way. We go […]
Trust, Insiders and Colossal Damage

“Trust no one, Jim. Especially not in the mainstream;” said Mr. ‘Control’ to Jim in an opening scene of John Le Carre’s ever so popular 1974 British fiction spy novel: Tinker Tailor Soldier Spy. Jim was a part of the British Intelligence Services, code-named ‘Circus’, sent by ‘Control’- head of the ‘Circus’, on a mission […]
