Overview
In the backdrop of increasing digitalization, the number of endpoints are also increasing.
And as the number of employees, working both remotely and on-prem, have started using their personal devices for work, it has been highly critical to ensure that each and every device in the workplace is secured from misuses. In the modern IT environment, more devices are inter-connected for different tasks at different levels in the network. As a result, it results in more avenues for cyber attacks. The need for endpoint security management comes here.
Why is it getting increasingly important?
Almost 81% of organizations revealed that endpoint security is the ‘most sought after’ security in complex IT infrastructure today. The increase of BYOD practice has made data access more fluid in almost all areas in the IT ecosystem.
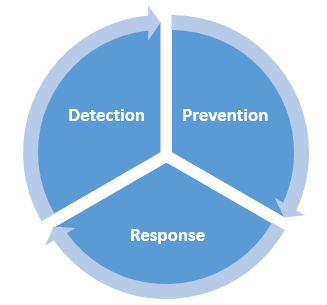
The endpoint security management is built up on the foundation of three pillars where unauthorized and suspicious end-users are detected and prevented from allowing access to the critical enterprise network base. Post-detection, the IT threat detection team receives notifications about the login attempts so that necessary security actions are taken before it’s too late. In this regard, very often, the benefits of Endpoint Security are mistaken with the benefits of Anti-virus software. Endpoint security approach in an organization makes endpoints more responsible for security whereas anti-virus software just secures the network.
Where are the risks?
According to Forbes, 70% of the most successful breaches originate at the endpoint. In the current Work From Home (WFH) scenario, most of the employees perform critical IT tasks through internal networks from endpoints without any restriction. As a result, the access control risks rise exponentially. Since endpoints ensure interconnection of every device in the network, the vulnerability of cyber threats in and around the endpoints increase alarmingly.
What are the accrued benefits of Endpoint Security Management?
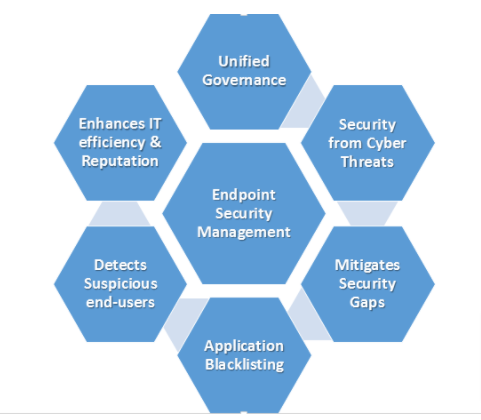
An endpoint security management can ensure a unified approach to manage and secure endpoint devices. From the administrators’ point of view, the organizations can reap the following benefits with the right solution deployed at the right time:
- Unified Governance — A robust endpoint security builds the framework to govern end-users accessing critical devices.
- Security against key cyber threats — Once endpoints are protected from key cyber threats, the IT environment becomes safer and customer engagement improves.
- Mitigate security gaps — Improved visibility of endpoints on the network periphery, eradicates security gaps that could have been the reason for security breach incidents.
- Application Blacklisting — It is extremely necessary to allow application access to the end-users based on daily use cases where the security mechanisms blacklist harmful or useless applications in the network.
- Detects suspicious end-users — A robust endpoint security detects suspicious end-users in real-time and prevents allowing access to critical applications.
- Enhances IT efficiency – When endpoints are safe and secured from malefactors, the organizations can ensure an efficient IT environment
Conclusion
Managing devices both on-prem and remotely raises serious security concerns and questions. Endpoint governance and robust access control policies help organizations to get rid of the endpoint vulnerabilities. Hence, it is time to reinforce strong endpoint security management.

